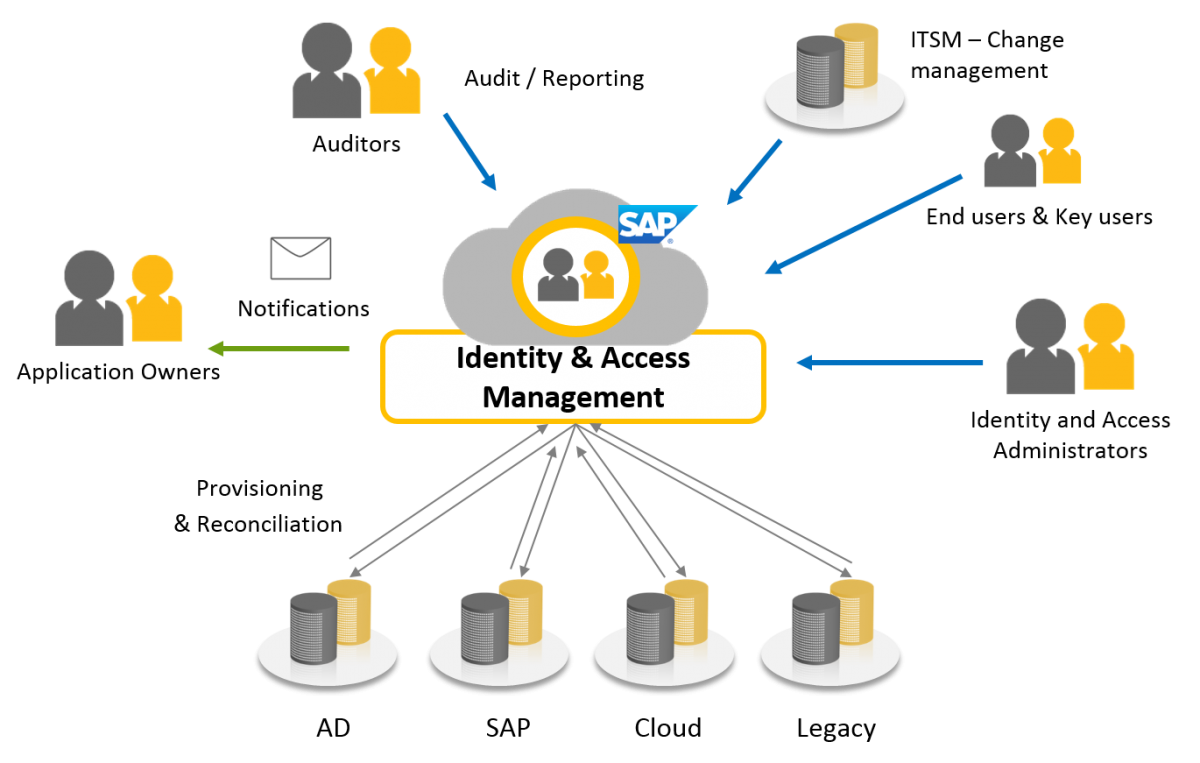
Information technology managers can use Identity Management and Access Control to manage user access to network information. The framework of business processes, policies, and technologies are designed to manage the digital identities of users. Identity and access management products allow system administrators to control access to systems and networks based on users’ roles within the company.
Defining Identity Management and Access Control
Identity and access management (IAM) is an enterprise IT security component that ensures users have the necessary access and that the systems, data, and applications can’t be accessed by unauthorized users.
Users could be customers (customer identity management) or employees (employee identity management). IAM systems define the digital identity of every individual user, and continuously maintain, modify, and monitor these digital identities throughout the access lifecycle. These systems grant the right access to enterprise assets to the right people at the right time while ensuring compliance with government regulations and corporate policies.
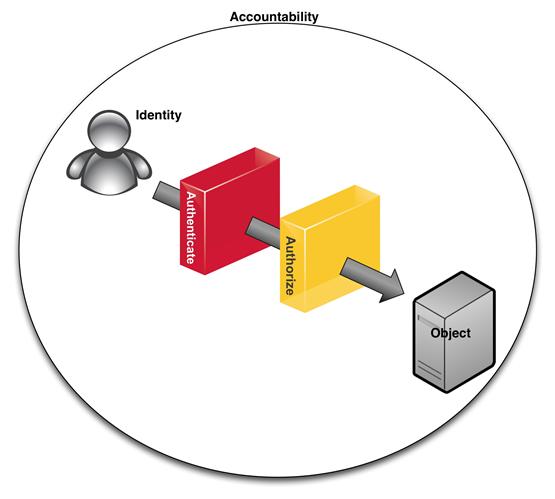
What IAM Systems Should Include
IAM systems should include all the tools and controls necessary to capture and record user information, manage the database of digital identities, and facilitate the giving and revoking of access privileges. A centralized directory service that gives oversight and total visibility of the user database is essential to an IAM system. These systems should reduce the time of and simplify the account setup process, reduce the potential for system abuse, and allow administrators to view and change access rights instantly. IAM systems should balance the speed and automation of monitoring and modifying access rights.
There are three typical systems used for Identity and Access Management:
- Single Sign-On (SSO): this access and login system permits users to go through a one-time authentication process and grants them access to the necessary software, systems, and data without individually logging into each area.
- Multi-Factor Authentication: this system combines something the user knows, something the user has, and something the user is. Multi-factor authentication requires a combination of a password, security token, and a fingerprint to authenticate users and grant appropriate access.
- Privileged Access Management: this system integrates the employee database and pre-defined job roles to grant the necessary employee access to perform their jobs.
IAM technology can be applied in different ways from one organization to another. Practical applications for providing IAM technology include on-premises, through a cloud-based model, or via hybrid cloud setup.
OneLogin is the identity platform for secure, scalable, and smart experiences that connect people to technology. The IAM solution allows customers to connect all of their applications, identify potential threats, and act quickly. The identity and access management platform grants users easy access to applications through a single-sign-on portal, provides lightning-fast user provisioning, remote access to applications, and smart AI-powered authentication. Secure and centralize your applications, devices, and end-users all-in-one-place with OneLogin and keep your organization protected.
The Benefits of IAM
IAM technologies streamline the role of IT managers by capturing, recording, and managing digital identities and their access permissions automatically. Businesses can give non-employee users access to their networks across mobile apps, on-premises apps, and software-as-a-service apps securely. IAM technologies improve collaboration, enhance productivity, increase efficiency, and reduce operational costs.
Identity Management and Access Control technologies have several benefits for businesses:
- One policy interpretation is used to authenticate, authorize, and audit users in order to grant access privileges.
- Properly managing digital identities gives greater control of user access and reduces the risk of data breaches.
- Automating IAM systems improves operational efficiency by requiring less effort, time, and money to manage networks.
- IAM framework makes it easier to enforce user authentication, validation, and privilege policies.
- Companies can better comply with government regulations by providing proof that corporate information is being properly used.
Adopting Identity Management and Access Control technologies is one of the best practices a business can implement when it comes to network security.